Firmware Analysis For Iot Devices
More than 90 of firmware files analyzed by IoT Inspector contain critical vulnerabilities. IoT devices have already outnumbered the worlds population.

5 Easy Ways To Better Iot Security Cyber Security Awareness Cybersecurity Infographic Iot
Next we need to acquire the firmware file for this IoT camera.

Firmware analysis for iot devices. This is the first simple way to not only examine the IoT devices firmware for vulnerabilities but also the compliance with international security standards without requiring access to source code or network or physical access to the IoT device. Firmware is a potential security issue on PCs servers IoT devices network routers and a lot of other equipment. In this paper a searchbased firmware code analysis method is proposed to associate the program functionalities with the assembly code.
Manufacturers usually provide user guides with instructions for manual software update or in the case of bricked hardware. We discuss our experience and lessons learned from analyzing USB. With this technique you can emulate a Firmware originally meant to be run on a different architecture and interact with it even without having a physical IoT device.
Crucial for IoT In the early days of IoT in order to make any firmware updates you had to retrieve the device take it apart connect it to your computer reprogram it put it back together and return the device to the field. IoTconnected device firmware security analysis platform Firmware security. A huge challenge Majority of organizations have security testing and risk assessment tools in place to continuously scan and monitor their cloud infrastructure and applications running on top of it.
Wir wissen worauf es bei Ihrem IoT Projekt ankommt. The preferred tool for. OTA Firmware Updates.
Originally developed together with experts from SEC Consult it operates as a cloud-based vulnerability scanning platform that analyzes the firmware of IoT devices. Anzeige Vom Konzept bis zum Betrieb. All connected IoT devices could be updated in a controlled timeframe.
Rule-driven push mode enables multiple- use cases such as-Auto push of firmware updates upon attacks if any on a device model-Auto rollback of a previous version upon firmware issues. Every modern computing device is usually composed of six to seven --. PROS Enterprises industrial IOT or users.
Firstly download the latest firmware from the device manufacturers website often found in the support page related to that device. Firmware Emulation can serve a number of different purposes such as analyzing the firmware in a better way performing exploitation performing remote debugging and so on. In this post we will have a look at how we can perform Firmware Emulation of a given IoT device.
Default credentials are the number 1 vulnerability exploited by hackers to hijack your IoT devices. Next we need to learn a little bit more about the firmware file we have downloaded. In this article we examine the chal-lenges of firmware analysis for the IoT era.
As this device is updated manually we need to go to the D-Link support site and download the firmware file linked above. IoT Inspector is a platform for automated security analysis of IoT firmware. As such firmware analysis for these devices is getting more critical and urgent yet there is no systematic way to assess the wide variety of firmware that exists across the IoT universe.
Our specialists can provide a quick overview of your security posture because typical vulnerabilities can easily be detected. Built to scale regardless of organization size and use case Binars IoT Firmware Analysis and Monitoring platform provides full automation and integration with both DevOps and SecOps pipelines to improve IoT device security throughout its lifecycle. This is how we do it.
In the experiment the firmware of Siemens PAC4200. However it is hard to investigate firmware due to the lack of source code and the complicated structure. Firmware Emulation can serve a number of different purposes such as analyzing the firmware in.
The firmware vulnerability is one of the most serious threats for Internet-of-Things IoT security. Wir berzeugen mit langjhriger Expertise ber 70 Mitarbeitern. 8 PROS Efficient in the case of small-sized updates.
The Key To Everything Firmware On Iot Devices Puffin Security
Firmware Updates Over The Air Developer Portal
Autohoney I Iot Automated Device Independent Honeypot Generation Of Iot And Industrial Iot Devices
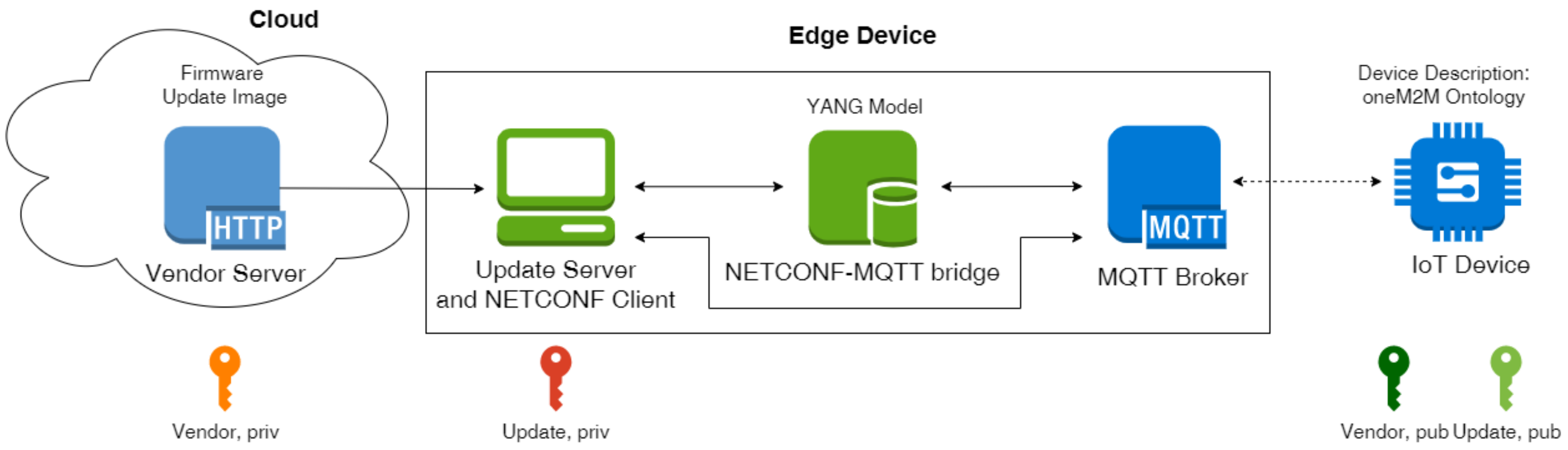
Sensors Free Full Text Mup Simplifying Secure Over The Air Update With Mqtt For Constrained Iot Devices Html

Automating Your Firmware Upload Device Cloud Configuration And Monitoring For The Iot World Iotready
Firmware Analysis For Iot Devices By Attify Simplifying Security Medium

Percepio S Device Firmware Monitor Is A Game Changer In The Rise Of Iot It Enables Instant Feedback From Systems Deployed In Th Webinar Iot Quality Assurance

Iot Firmware Update Prototyping Scenario Download Scientific Diagram

Iot Firmware Update Prototyping Scenario Download Scientific Diagram

Iot Device Firmware Analysis Omar Minawi

3 Top Iot Security Architectures And How To Fix Them Security Architecture Iot Cyber Security Awareness

Plug And Play Sensor Architecture For Iot Low Power Devices Download Scientific Diagram
How To Choose The Right Firmware Architecture For Your Iot Device Locolabs

Firmware Over The Air What Is Behind

Rak811 Good Choice For Lorawan Modules With Open Firmware Click Link For Open Source Project Https Github Com Open Source Projects Analysis Firmware
Firmware Update Verification Process 3 Iot Device Receives The Ota Download Scientific Diagram

Here S How To Hack Smart Bluetooth Locks And Other Iot Devices Check Out This Video From Pwnie Express Bluetooth Lock Iot Computer Security

Internet Of Things Tipsographic Internet Iot Zigbee

Firmware Analysis Toolkit By Attify Emulating Iot Device Firmware Youtube
Post a Comment for "Firmware Analysis For Iot Devices"